The email encryption market is set to grow by $ 4.9B during by 2025, progressing at a CAGR of over 22% from today. The reason for this growth, outside of the obvious need in defense against cyberattacks, is because hosting solutions like Microsoft Office 365 do not provide enough security. While many of Mailprotector’s managed service provider partners are using Microsoft products as part of their email hosting stack, Office 365 email encryption misses the mark in both features and in its encryption methods. In this article, we will explore why Microsoft’s 365 product falls short of the standard for email encryption. We will also discuss why a specialized email security approach is necessary.
When talking about a complete email security solution, email encryption must be present. Particularly for those administrators whose end users are regularly emailing sensitive data. What you’ll find is that Office 365 is restrictive and its email encryption feature is incomplete. Why? Let’s start with email encryption basics.

Basics of Encryption
Email encryption has become a necessity when sending emails outside of an organization. Lawyers, CPAs, medical offices, government officials, and others are required to send sensitive information across the Internet directly to their customers.
While Office 365 email encryption can be turned on and configured within Microsoft’s 365 platform, encryption is an afterthought to an otherwise top quality email hosting tool. As you’ll find, when sending encrypted emails outside of the Office 365 environment, things start to fall apart.
Email encryption allows for data to be protected by a digital security key while traveling publicly on the Internet. This prevents potential malicious hackers from accessing data you wouldn’t want visible to the public.
Office 365 email encryption can come in a few different forms, depending on your client and user needs – each of which can potentially leave your users exposed.
There are three standard types of email encryption available through Office 365: OME, S/MIME, and IRM encryption. Each of which has its respective security disadvantage. We believe that ignoring the downfalls of Microsoft’s email encryption is a recipe for disaster.

Why Office 365 Message Encryption (OME) Is Not Enough
Built on Microsoft Azure, Office 365 Message Encryption (OME) is the standard Office 365 encryption product provided by default to E3 and E5 license holders.
Email Usage Cannot Be Restricted
One of the biggest drawbacks to Office 365 email encryption setup and usage is that the OME product requires the Information Rights Management (IRM) or Azure Information Protection (AIP) add-on for administrators to add usage restrictions within O365’s system.
Usage restrictions would allow administrators to automatically restrict forwarding, printing, or downloading an encrypted email. The IRM and AIP products typically are an additional charge on top of the OME product, and without these products, the recipient of an encrypted email can do what they’d like with the email. So right out of the gate, Microsoft forces administrators to add products in order to be more secure.

Why Secure/Multipurpose Mail Extensions Is Not Enough
S/MIME encryption has been around since 1995. Because it has been around for decades, it is a go-to for large organizations that want to manage their data encryption.
While S/MIME encryption allows a public key to be provided to anyone, the downside is that each person would need their S/MIME key installed on their computer. On top of more work, the S/MIME key prevents O365s systems from scanning emails sent this way for malware and viruses.
S/MIME encryption requires a certificate on each user’s computer or email client to decrypt emails sent this way, but once the leg work is out of the way, email can be kept secure from any prying eyes. In the early years of S/MIME, the main concern was that if a private key was lost, you’d also lose any email encrypted by S/MIME. Luckily there are free services available for key management, and many systems can help reissue a key to decrypt those emails.
S/MIME Makes Email Malware Scans Difficult
Office 365 allows S/MIME keys to be used. However, with S/MIME, it is difficult to scan the emails for potential malicious payloads. This includes viruses, malware, and bad links.
The inaccessibility and inflexibility of S/MIME emails is why people have gotten away from using it as a standard in their businesses. If you are archiving email for compliance or hope to scan incoming emails from the Internet, S/MIME encryption can make this difficult and put users at risk.

Why Information Rights Management (IRM) Is Not Enough
IRM Cannot Be Used by All Email Platforms.
The Microsoft 365 IRM product allows an end-user to restrict what a recipient of an encrypted email can do once an email is opened. This service prevents any data leakage from the end-users who are not under your management.
The downside to IRM, in addition to its added cost, is that some platforms cannot receive email encrypted by the IRM system, so OME would be necessary for general use.

Why Office 365 Message Encryption is Not Enough
Microsoft Office 365 is an excellent choice as an email host. However, we recommend a specialized approach to email encryption to ensure complete email security. Without a full scale email encryption solution like Bracket, you are leaving your users exposed. Here are a few reasons why Office 365 email encryption isn’t enough.
Office 365 Cannot Do Email Recall
There are many features other products provide that OME and IRM don’t allow. These features include the ability to recall an email. One of the most requested options end-users want is to take back an email they didn’t want to send. OME encryption doesn’t allow for email recall.
Further, OME comes up short because it cannot give the end user the ability to manage a message thread. In addition to not being able to recall, once the email is out on the Internet, it is encrypted, but it can’t be adjusted or edited with OME or IRM.
Office 365 Message Encryption May Not Meet Email Compliance Policies
OME encryption utilizes RSA-2048 and SHA-256 for their encryption. Not many people mind this difference, but some regulatory bodies may require AES-256 encryption in the future, which is technically more secure than RSA-2048.
Office 365 Encryption Lacks Flexibility
OME can lack some flexibility that other encryption platforms have. Another factor many security professionals are concerned about is having all their data and mail flow in the same place. If you have all your services with O365, you have a single point of failure if anything breaks.
Microsoft is not untouchable. So, businesses can save time, money, and clients if they’re able to have a secondary system running in case O365 goes down. If you have encryption on another platform, many providers let you email from their encryption platform separate from O365.
In case of a Microsoft outage, this versatility will allow your end-users to keep working while Microsoft fixes the issues.
Additional Email Security Features Are Available Elsewhere
By using an additional email encryption platform, you could allow for the email to expire on a specific date, passwords to be added for concerned users, and subject lines to be protected when not in an encrypted state.
Bracket Email Encryption Picks Up the Slack
Mailprotector’s Bracket email encryption tool allows for automatic encryption, subject protection, forward protection, and download protection without any additional cost to the business.
Anything OME and IRM can accomplish, Bracket can perform as well, without the requirements of a high-cost license. So let’s talk about Bracket.
Bracket Encyption Does What O365 Cannot
The right email encryption tool can be a chore to select and manage. After listening to the needs of our Partner Advisory Board and other members of our partner base, we at Mailprotector decided to try something new. Partners were asking for an easier, faster way for users to exchange encrypted emails. They needed the process to be both simple and secure; both customizable and effortless.
Soon after, the Bracket email encryption tool was born and subsequently the technology was patented.
- Patented Encryption Technology: No one else can provide encryption quite like Mailprotector’s Bracket email encryption solution. Patented in 2020, Bracket was created as a secure, easy-to-use email encryption tool. To speak to Bracket’s ease-of-use, every user in the world can encrypt directly from their keyboard. Users simply wrap the subject line in brackets and send.
- Compliant: Bracket is compliant with HIPPA, FINRA, and many other regulatory bodies because it utilizes AES-256-bit encryption standards.
- No passwords, plugins, or downloads required: Recipients of emails from Bracket don’t need an account, a password, or even a one-time code to log in. It allows them to select a device fingerprinted link that logs them into the Bracket portal where your end-users have complete control.
- Email Recall Enabled: Emails can be recalled, expiration dates can be set on each message thread, individual comments and attachments can be removed, and the end-user can prevent any mismanagement of the email.
- Configuration Flexibility: Bracket can be configured in several ways. First, Bracket can be configured as an outbound gateway before emails reach the internet to encrypt data before anyone can intercept it. Second, it can be set up to be delivered directly via a secure connection within nearly any email client.
- No More Lost Passwords: Bracket offers users fool-proof sign-in with a secure, expiring link. That is good for both the users and administrators.
- Accessibility: Encrypted email can be sent from any email app on any device.
- MX-free for Office 365: No need to change records so they route through filtering services.
- Easy File Transfer: Bracket also includes an encrypted file transfer service, Bracket Share, which gives users a personalized file transfer page with an easy URL (share link) that they can provide to anyone.
- Quick and Easy Deployment: Bracket can be set up as a standalone product in O365 utilizing an API configuration between Mailprotector and O365. The deployment in any of these configurations takes only a few minutes, and IT professionals can leverage both Mailprotector’s DLP policies as well as O365’s, Google’s, or any others.
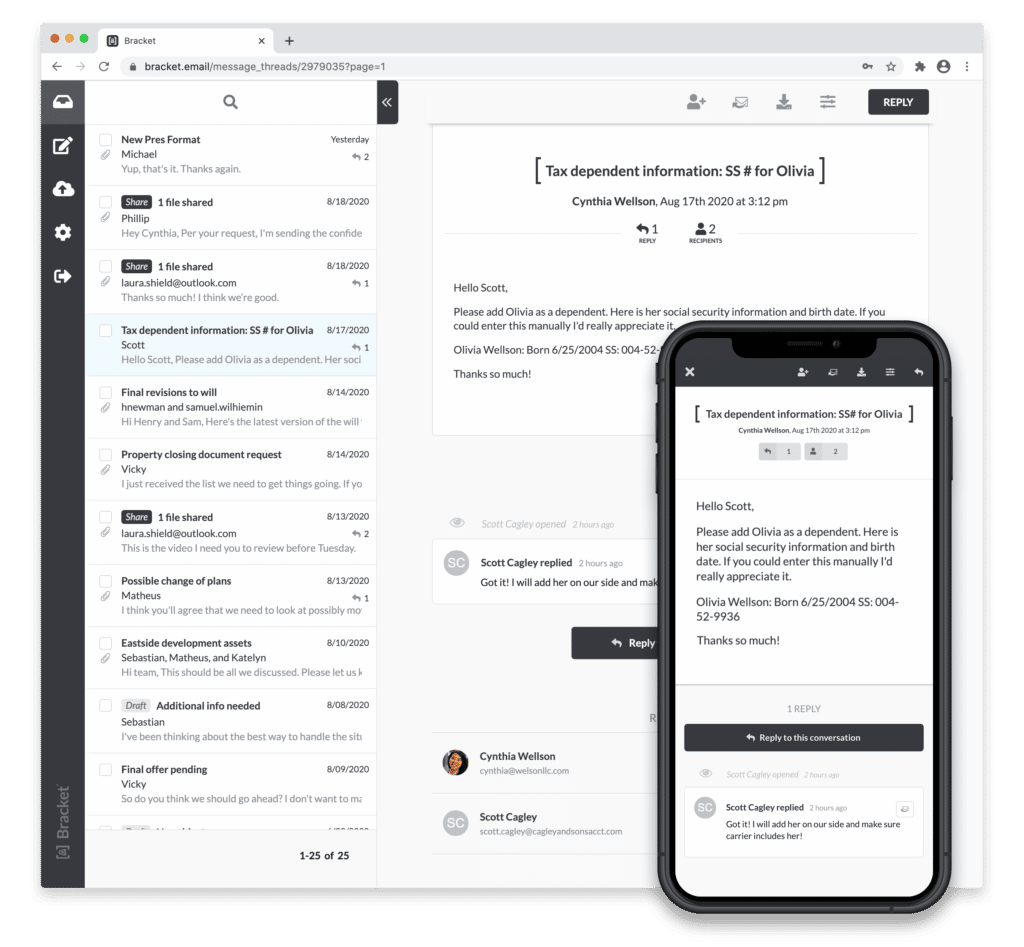
Bracket shores up everything that is missing from OME, IRM, and S/MIME while allowing you to get the best of both worlds in O365 and Mailprotector!
Does Office 365 have email encryption?
Microsoft 365 uses encryption in two ways: in the service, and as a customer control. In the service, encryption is used in Microsoft 365 by default; you don’t have to configure anything. For example, Microsoft 365 uses Transport Layer Security (TLS) to encrypt the connection, or session, between two servers.
What kind of encryption does Office 365 use?
Office and Microsoft 365 Message Encryption – OME
The first layer is Office 365 Message Encryption, or known as the acronym OME, and is encryption provided by Office 365. In 2018, Microsoft employs 256-bit encryption on their .docx files.