The average business email compromise (BEC) attack can cost a company hundreds of thousands of dollars, if not more. And according to the FBI’s Internet Crime Report, the frequency of phishing attacks is surging, at a 69% increase year over year from 2019. While there is no magic bullet to curb the increase, the best phishing protection solution is the combination of airtight phishing defense software with the frequent training and eduction of your users.

In this article, we explore:
- Phishing Attack Examples (feel free to copy and paste these for your users)
- How to Spot a Phishing Email (with example of CEO fraud)
- How to Spot a Phishing Email
- How to Respond if You Suspect a Phishing Email
- For MSPs and IT Administrators: Three Ways to Prevent Phishing Attacks
Phishing Attack Examples
What phishing examples should I communicate to my users?
There are new phishing examples happening every few months. However, here are several different examples of common phishing scams. Without question, the most common phishing method is conducted via email. This makes added protection against phishing, viruses and spam essential for any IT security stack.
Email-Based Phishing Attack Examples
- Spear Phishing – this email attack is very common. Someone with malicious intent has researched an organization and the people within it. The bad actor sends an email referencing a topic familiar to the recipient.
- Man-in-the-Middle – a threat actor emails two different parties pretending to be each, asking for sensitive information. This way, there’s a chance the story can be corroborated from one to the other.
- Clone Phishing – emails appear to come from popular institutions (ex: Bank of America), but email links are fraudulent.
- Clickjacking – bad actors conceal malicious links beneath legitimate hypertext.
URL-Based Phishing Attack Examples
- Pharming – fraudulent code redirects victims to fraudulent websites designed to look like the original.
- Watering Hole Phishing – links to employee-frequented sites are compromised.
- Evil Twin – Victims unknowingly login to a fraudulent, “free” Wi-Fi hotspot. For example, a malicious hotspot is set up near a coffee shop, called “Coffee Bean Guest.”
- Typosquatting or URL Hijacking – Fraudulent sites are created to capitalize on user misspellings when keying in the URL.
Other Phishing Attack Methods
- Voice Phishing (vishing) – A caller leaves a voicemail needing, you guessed it, personal information. Often callers, will impersonate institutions like a bank, the IRS or the Social Security Administration.
- SMS Phishing (smishing) – a texter asks the recipient to update important account details and offers a link used to steal personal information.
- Social Media Phishing – a hacker posts an irresistible link to a user’s social media page or post.
- Angler phishing – a hacker establishes a fake customer service account on social media, aiming to reach someone looking for support who will readily provide credentials.
More Cybersecurity and Phishing Terms
When talking about phishing, here are some other common cybersecurity terms you’ll hear.
- BEC (Business Email Compromise) – criminals send an email that appears to come from a known source with a legitimate, oftentimes urgent request for personal information (a CEO needing gift cards, a would-be vendor updating their mailing address, a title or mortgage company needing a down payment).
- Social engineering – when someone uses deception to manipulate people into divulging confidential or personal information that may be used for fraudulent purposes.
- Bad, threat or malicious actor – the person or group responsible for an event that impacts the cybersecurity of another entity.
- Malware – general term for any type of malicious software designed to harm or exploit any programmable device, service or network.
- Cyber Resiliency or Cyber Resilience – the ability of an organization to both respond and rebound from a cyberattack.
How to Spot a Phishing Email
One important way to spot a phishing email is to look for inconsistencies. For example, take this malicious email one of our partner success managers received earlier this month. The email was sent from a threat actor pretending to be David Setzer, Mailprotector’s CEO.

- Grammatical Errors: If you’re a wordsmith, you can spot several grammatical errors with this email, including misplaced commas and poor spacing.
- Generic Intro: Greetings without your name like “Hello” or “Dear Sir or Madam” are identifiers.
- Email Signature: Only we would know this, but the sender did not use an email signature consistent with what our company uses.
- Odd Request: Our CEO would never send an email like this. It is out of character that David would need something directly from Dallas with no detail and a hurried tone. This particular request is referred to as “CEO Fraud.”
Still unsure? Reach out to the contact you know directly using safe contact information to confirm the request. Do not forward the original email.
How to Respond if You Suspect a Phishing Email (For Users)
If you suspect a phishing email, here are some quick actions you can take.
- Delete the Email. Do not click any links. Do not open attachments. Report the phishing email to your administrator.
- Block the sender.
- Talk about it. When the phishing email example from earlier was sent, Dallas sent a Slack notification to our entire company to be on guard that a malicious actor was impersonating David.
Beyond ignoring the email. Microsoft Office 365 and G-Suite email security filters are not enough to handle today’s modern attacks. Work with your IT administrator to add extra layers of phishing protection.
Three Ways to Prevent Phishing Attacks
You could have the best anti phishing software in the world, but your network is only as protected as your least educated user. Despite this, you still need great tools to minimize risk for your users.
Here are a few anti phishing tools we recommend to help you prevent phishing attacks within your user communities.

Step 1: Train Users on How to Prevent Phishing Attacks
End user training is critical. The FBI lists common phishing attacks, the majority of which begin with spear phishing. Consider reviewing these with your end users.
Generally, to remain protected, your users will want to do the following:
- Get in the habit of looking at contact information to ensure accuracy. Often, phishers will alter a letter in an email (like subbing an “n” for an “r”) or show the correct sender name “ex: John Smith” while the email address will be fraudulent.
- Be wary of links and clickable images. Remember that seemingly valid hypertext or shortened links can be fraudulent, as they could mask the illegitimate link.
- Be critical of abnormal C-Level and colleague Requests: malicious actors will impersonate a senior executive like the CEO asking employees to do things like purchasing gift cards or clicking links.
- Monitor caller ID and returning voice calls using trusted contact info. Did the caller leave a voicemail? Call or instant message your potentially impersonated colleague directly to confirm validity.
- Use Multi-Factor Authentication where applicable. If your help desk receives a call from a user requesting their login credentials, you might consider using MFA. Or maybe you could let the user know for security purposes you’ll be hanging up and calling them back at the number you have on file for them.
Companies like KnowBe4 provide end user training modules that keep your users up-to-speed and mindful of the latest phishing tactics.
Step 2: Invest in Anti Phishing Tools
As an MSP or MSSP, you are balancing and supporting a cross section of IT solutions. Each with their own respective dashboards, nuances, and help desk tickets. As a creator of one of the best phishing protection solutions on the market, here’s what we took into consideration when developing CloudFilter.
- It must protect against phishing, spam, and viruses. You have a full technology stack to manage. Why not consolidate phishing, spam, and virus tools by investing in one tool that does it all?
- It must allow administrators to manage multiple mailboxes at once. Multi-tenant management is critical so you can set rules for the entire organization.
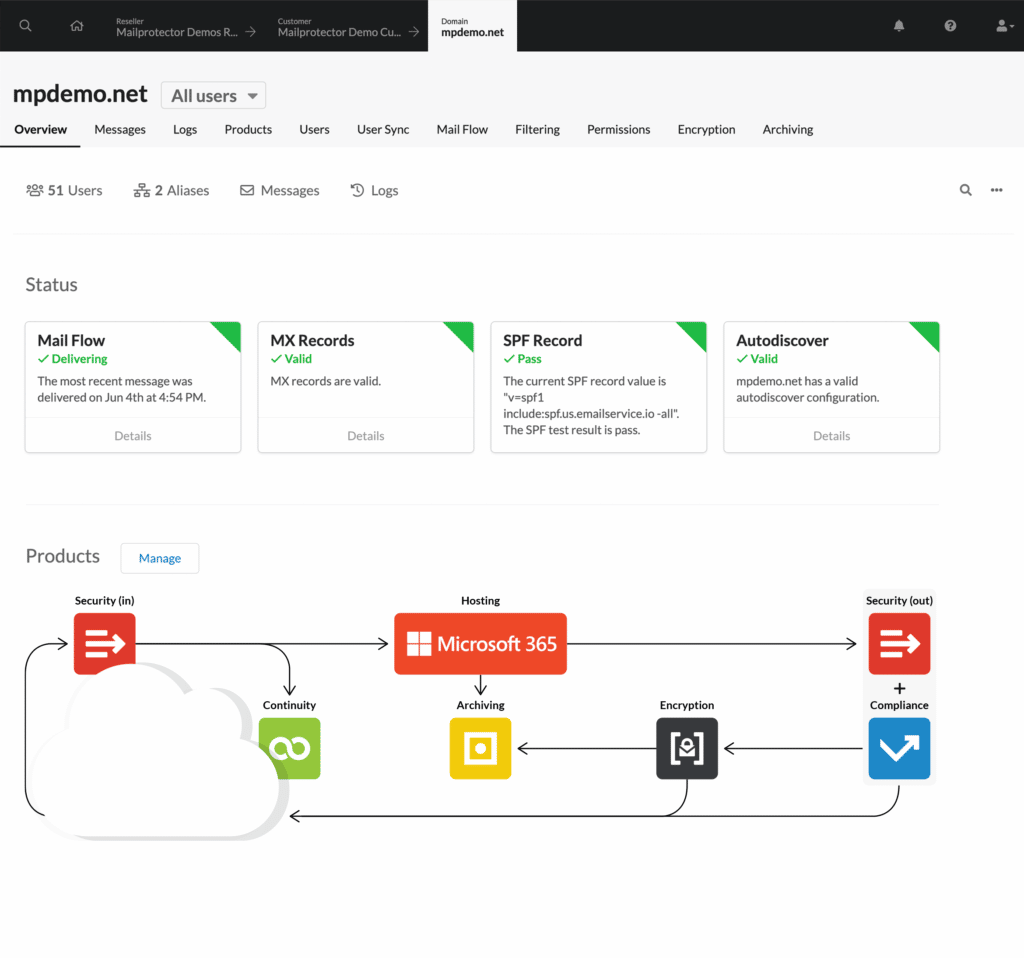
- It must be secure, yet simple. There are a lot of feature-bloated, complex tools out there. Choose something clean and easy to manage. For an example, see CloudFilter’s dashboard below. We received feedback from our MSP partners on how they wanted the portal to be designed so we designed this with the MSP administrator in mind.
Optional: Consider Mandating Email Filtering for Your Customers
You are leaving yourself vulnerable if you aren’t making email filtering mandatory. We have had several partners lately tell us they’re making email filtering mandatory for anyone they support. Operating without a proper phishing defense tool is like driving without insurance. Sure, it can be done but what happens when an accident occurs?
Step 3: Invest in an MSP-Backed, US-Based Email Security Partner
Don’t let a successful cyberattack happen on your watch. Instead, take the necessary steps to secure your end users with an anti-phishing product designed specifically for MSPs and MSSPs by a US-based company who specializes in email security.


















