Cyberattack Detection and Prevention 101
The purpose of this written series is to, first and foremost, provide immediate guidance to anyone who may have been a victim of a cyberattack. Here, we offer tips, best practices and written assistance to those who may be asking the question, “have I been hacked?” We will offer suggestions for those who may trying to figure out how to prevent cyberattacks, including the start to building an incident response plan.
Mailprotector is an email security company who exclusively supports a diverse base of managed service providers and IT security professionals. Businesses count on these IT professionals to keep them secure, so our partners need to be able to count on us to deliver unparalleled email security. We are not an organization who will remediate cyberattack, but here we will offer some guidance on what you can do if your organization is the victim of a breach.
It is well documented that data breaches are expensive. According to a study conducted by IBM in 2021, “Cost of a Data Breach,” data breach costs rose from USD $3.86 million to USD $4.24 million, the highest average total cost in the 17-year history of this report.
Recent Cyberattack Example: Here’s how it happens
- Threat actor sends email containing a malicious link or attachment.
- User accidentally opens the link or attachment, releasing the malware on the company network. The type of malware used will grant the hacker access to the organization. One example of a penetration-testing software Cobalt Strike, which was innocuously designed to aid IT professionals with cybersecurity. Unfortunately, hackers also use it for their benefit, deploying an agent named “Beacon” on the victim’s machine to launch an attack.
- Through this, now exposed gap in the company’s network, the threat actor has a look around the network, getting their prying hands on everything they can – valuable or not.
- The hacker can then access all workstations on the domain by way of active directory.
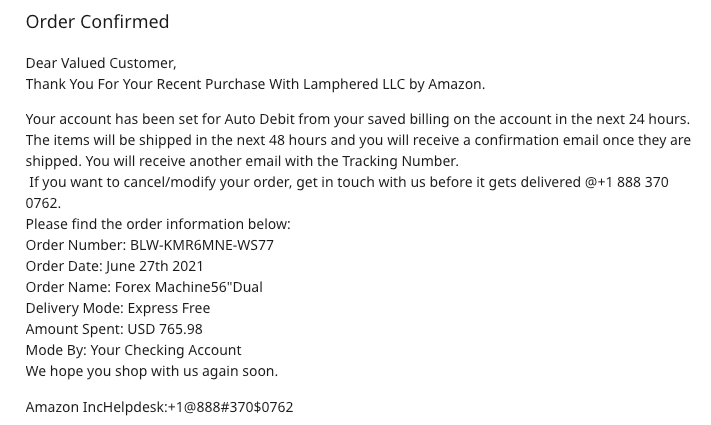
Spear Phishing Example: Lamphered LLC Amazon Scam
There are thousands of examples out there of phishing scams. We list types of phishing attacks on our blog, Select the Best Phishing Protection Solution for Your Users. But here’s a good recent one that has hit a few of our Gmail accounts lately.
How the Lamphered LLC Amazon Scam Works:
Here’s a recent scam, targeting email users who are paying attention to their household purchases. Someone may unwittingly reach out to the hackers directly intending to talk to customer service. The hacker, masquerading as Amazon customer service, takes some quick personal information from you, and that’s a wrap.
How to know if you’ve been hacked
So, how do you know if you have been hacked? Here’s a list of things you might observe on your network if you have been compromised.
- Unusual outbound network traffic.
- Increases in database read volume.
- HTML response sizes.
- Large numbers of requests for the same file.
- Mismatched port-application traffic.
- Suspicious registry or system file changes.
- Unusual DNS requests.
- Login Red Flags.
- Unexpected system patching.
- Mobile device profile changes.
- Bundles of data in the wrong place.
- Web traffic with inhuman behavior.
- Signs of DDoS activity.
- Irregular activity in privileged user accounts.
- Decrease in Internet speeds.
- Review network, looking for any connected devices that are not familiar.
For more, the Digital Guardian blog offers more information about Indicators of Compromise.
Still asking “have I been hacked?” Let’s go through some email security-related questions to see whether your email has been compromised.
Has my email been hacked?
Related questions help desks get during and around a breach, outside of “have I been hacked?,” are, “is my email compromised?” or “has my email been hacked?” Here are a couple of quick indicators that a user’s email is compromised.
- Unfamiliar geographic access.
- Passwords not working.
- Users receiving password reset emails they did not request.
- People are receiving emails or social media invites not sent by the user.
- Appearance of new browser toolbars, applications, or software the user did not install.
- Devices acting strange – things like unexpected restarts or redirected Internet searches.
- Your anti-virus, anti-spam, or email filtering controls have been disabled.
- Changed email passwords.
- Lost access to social media, service provider, or application accounts
- Sent or trash folders contain emails you didn’t send.
- Messaging rules added to your email account – forwarding and deleting emails for instance
These are great indicators to let you know if your email has been hacked. So, what do you do if you, in fact, have been hacked? Read “What to Do if Your Network is Hacked.”
Has my website been hacked?
What are the signs that a website has been hacked? There are two main ways hackers gain access to your website: passwords and a vulnerable structure. Here are a few ways to know whether your website has been hacked.
- Website is blacklisted by Google, Bing, Yahoo, etc.
- Host has disabled your site.
- A warning when visiting your site such as “this site contains malware.”
- New administrators and users have been created without your knowing.
- Website rendering strangely.
- Website redirects to a different URL; website might still look “normal”
- Ad-blocking software hides most images on your website unexpectedly
So, what do you do if your website has been hacked? Read “What to Do if Your Website is Hacked.”
Before an Cyberattack Occurs, Create an Incident Response Plan
No matter how good you are at your job, if any of your users incur a cyber attack, it is going to be a stressful situation. And hackers don’t care about your family vacation or your weekend, either. In fact, organized cyber attacks happen regularly on weekends because of the increased chance that no one is watching.
Think ahead – during a time when you aren’t under duress. That way, should you ever encounter a cyber attack, you can calmly pull out your plan and get to work.
Mailprotector has created some thoughts for you to use as a template for an incident response plan. Feel free to pull a little from here and a little there to create your plan. You’ll also need to think about things that will need to be attended to that are unique to your business and your security stack.
Who is Mailprotector?
Mailprotector is an email security, email privacy, and email encryption company whose goal is to provide the best, most complete email security option we can to our base of partners. From where we sit, we see a vast array of businesses jumping into the IT security space because “cybersecurity” is the latest buzzword. Since 2000, we have been patenting, building, and evolving the most secure email security platform available on the market today. Don’t settle for a partial email security solution.
Schedule a demo to see what a complete solution looks like today!

BONUS RESOURCE
Preventing Ransomware Attacks eBook (PDF)
Read an in-depth summary where we look at several recent ransomware attacks to break down exactly what happened, which ransomware prevention plans worked, and which ones didn’t hold up when it mattered the most.



















